Trivy: Enhanced with AWS scan integration
Trivy now supports scanning AWS resources for security misconfigurations
Trivy is one of the most reliable open-source tools for image scanning. Primarily famous for its incredible image scanning, it also supports scanning Kubernetes clusters/resources, file systems & git repositories for misconfigurations & security vulnerabilities.
Thanks to Anaïs Urlichs for inviting me to the beta & early adopters review.
As of Aug 15, 2022, Trivy is capable of scanning AWS resources for misconfigurations. The less known fact is that aquasec acquired cloudsploit, a Cloud Security Posture Management (CSPM) tool that supports AWS, GCP, Azure, Oracle, etc. It even covers standards like HIPPA, PCI & CIS benchmarks. For unforeseen reasons, cloudsploit didn't receive any updates since Aug 26, 2020. Nevertheless, now trivy can perform scans cloudsploit was capable of & beyond.
Hands-on
Kindly note that this is still an experimental phase. As of this writing, Trivy supports scanning 31 types of AWS resources for misconfiguration.
Authenticate to AWS account
aws configure
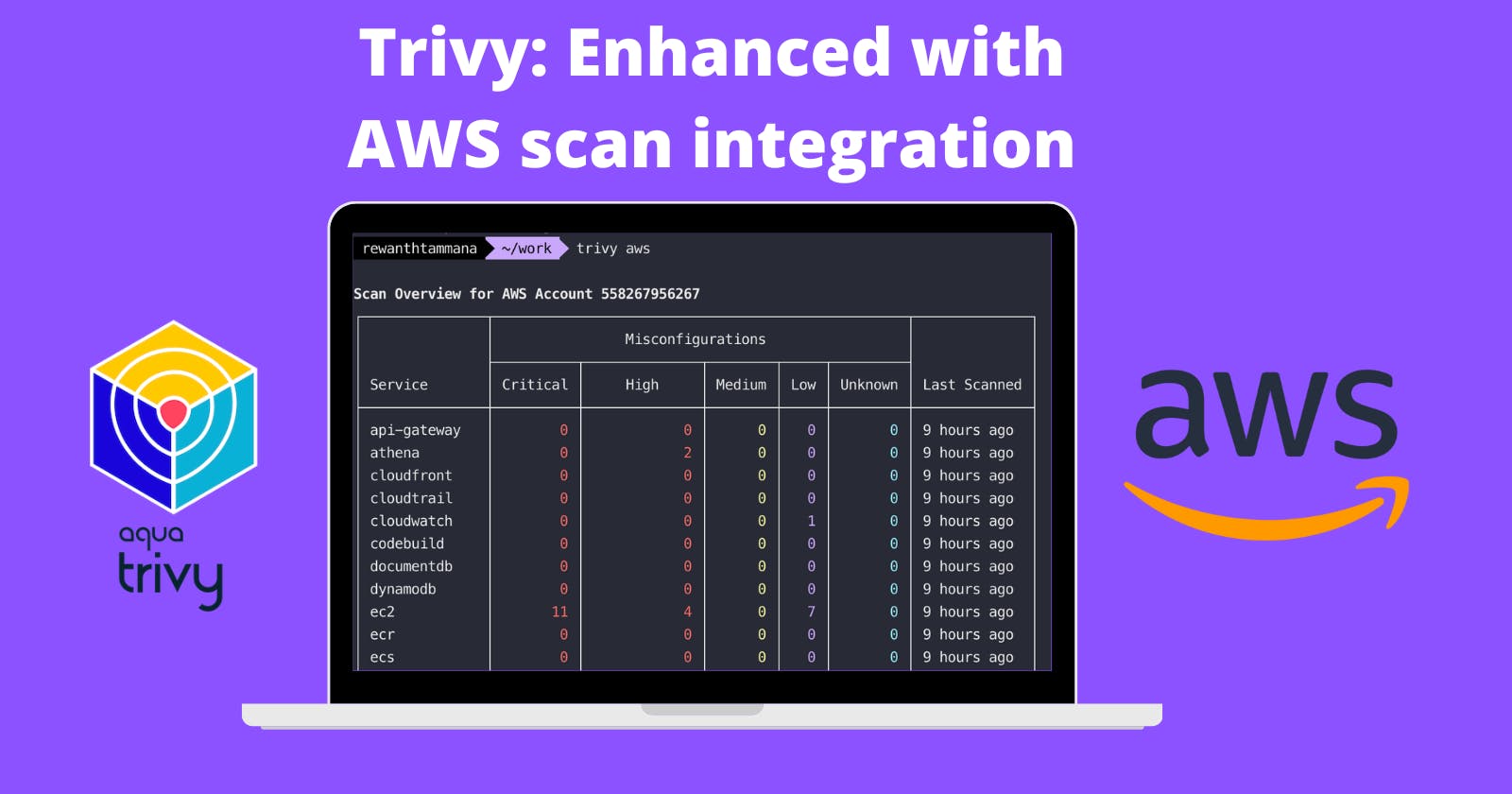
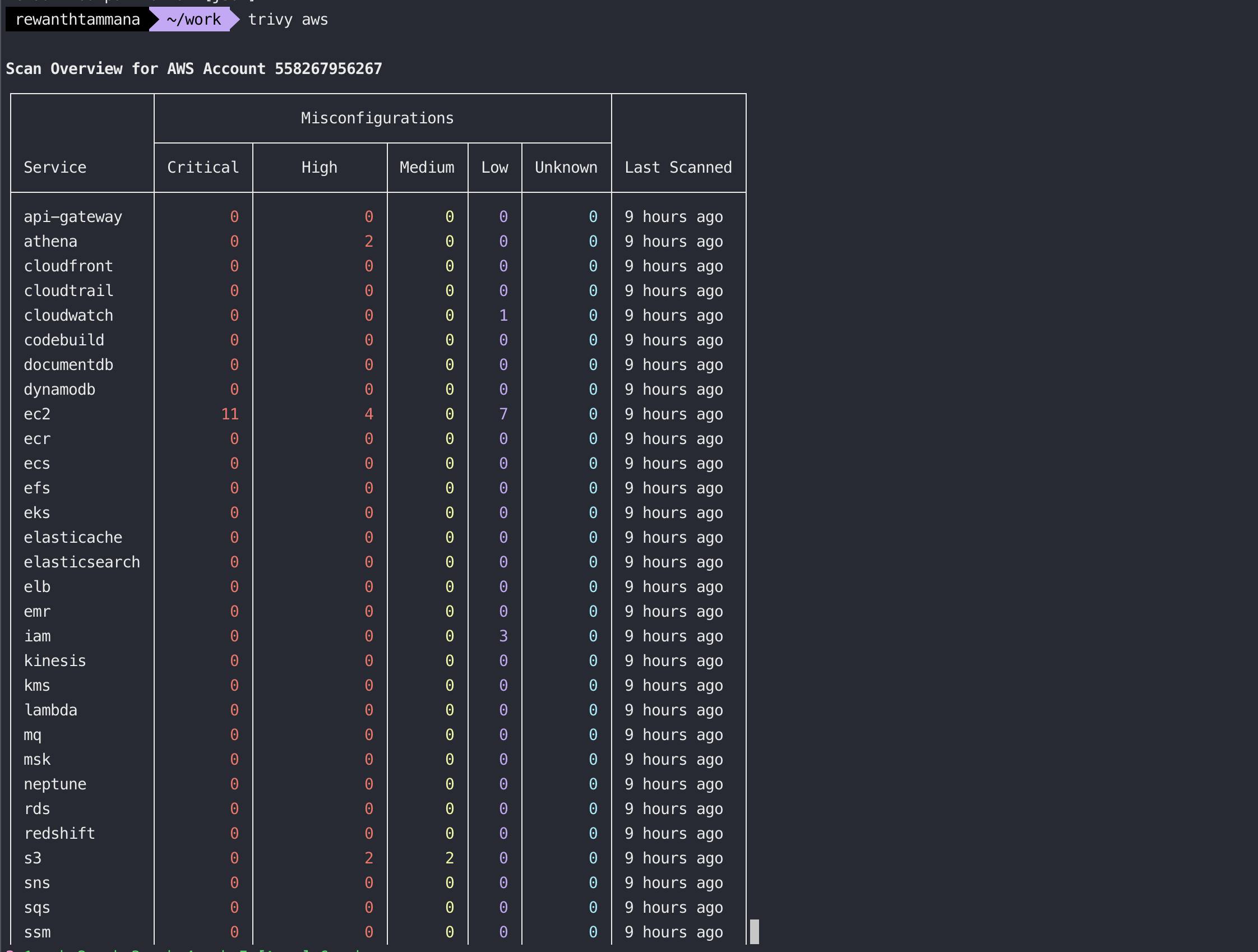
Scan all resources in the default region
The region set during aws configure will be picked up! This returns the summary/count of misconfigurations for supported resources.
trivy aws
Scan all resources in a specific region
trivy aws --region=us-east-1
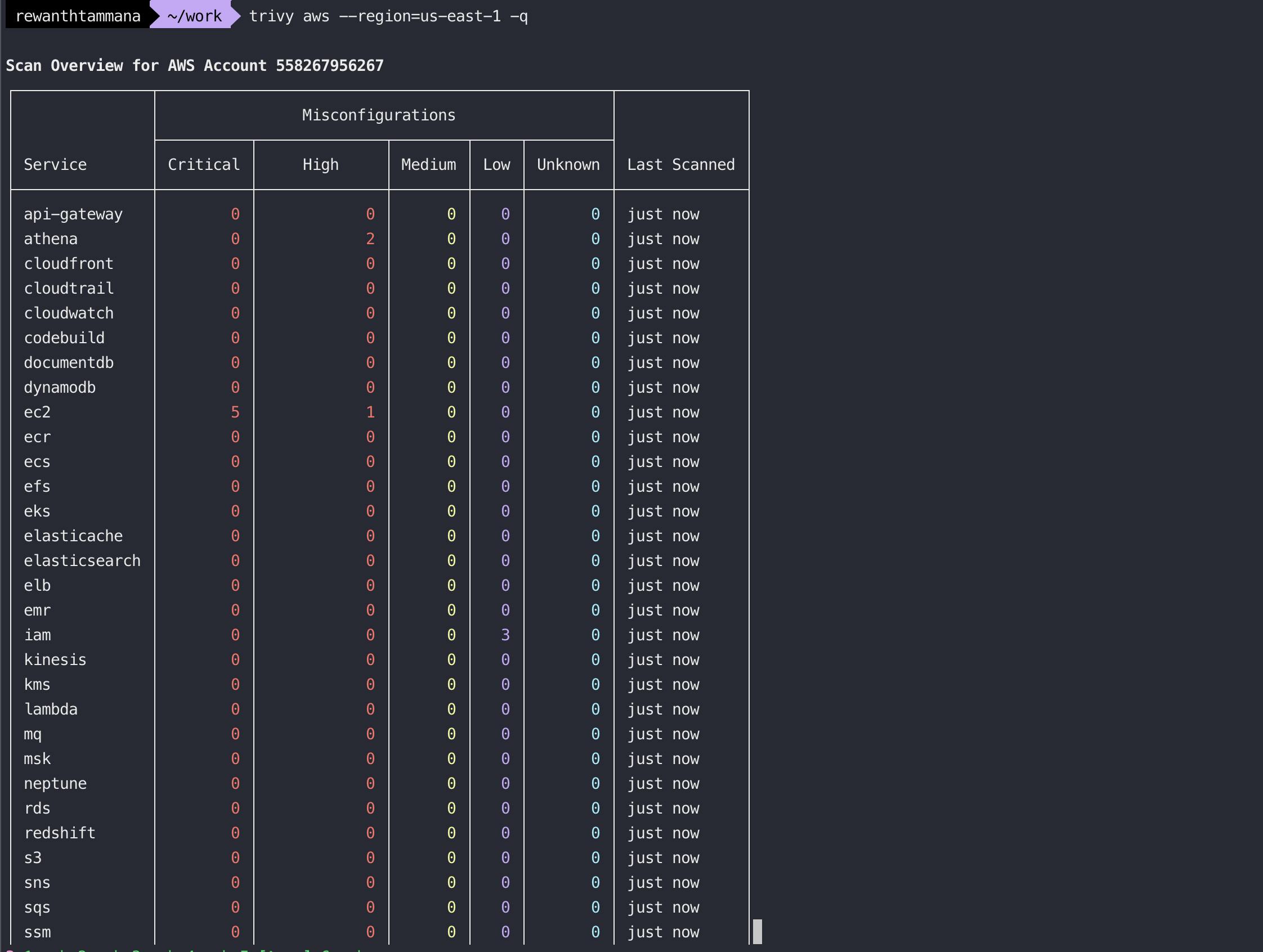
The list can be lengthy and exhaustive to understand. The service feature comes to the rescue.
Scan a single resource
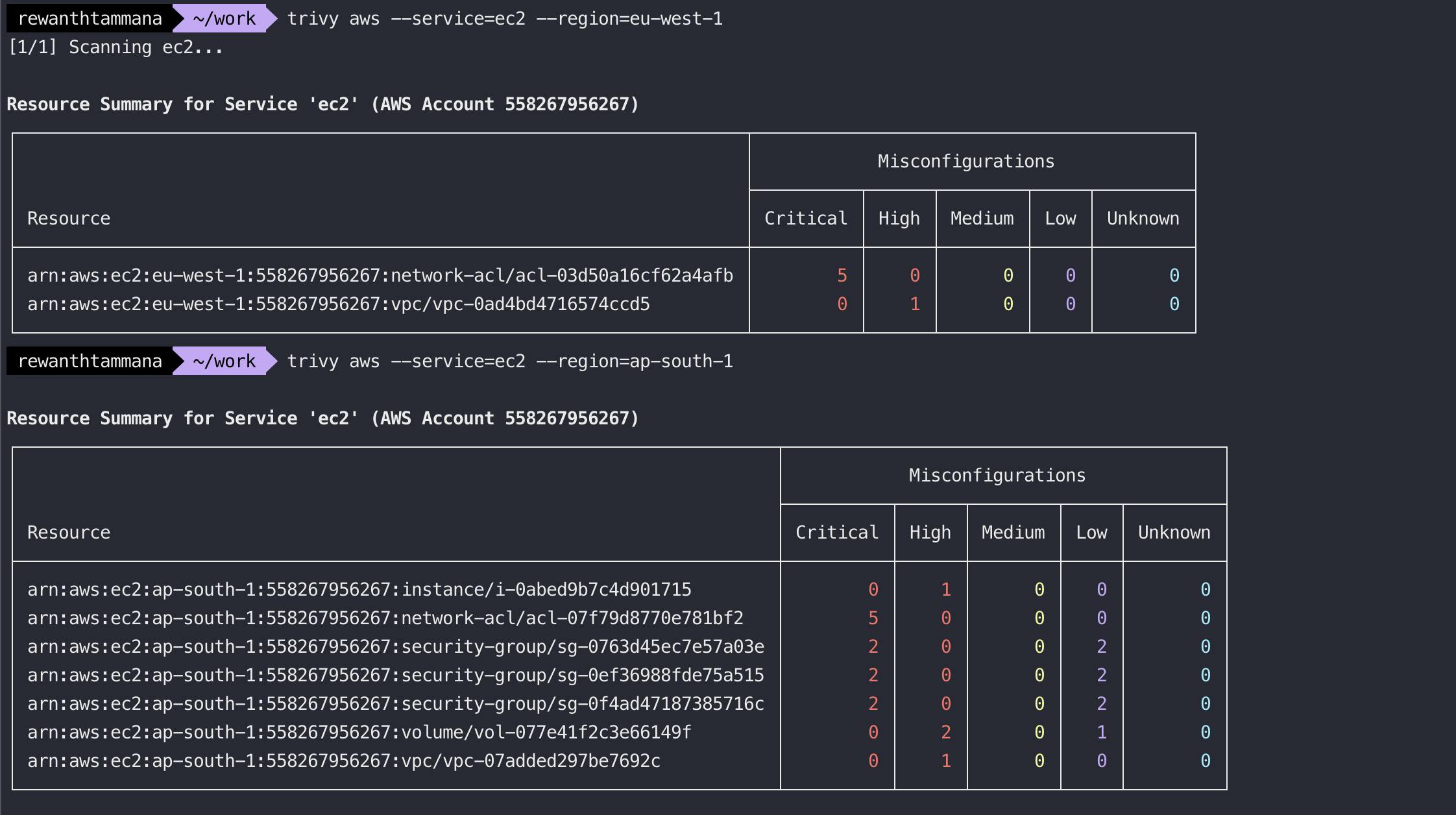
The service feature shows more information on the misconfigurations.
trivy aws --service=ec2
trivy aws --service=ec2 --region=eu-west-1
Format output
Trivy supports multiple output formats, table, json, sarif, cosign-vuln, github, spdx, cyclonedx & lot more.
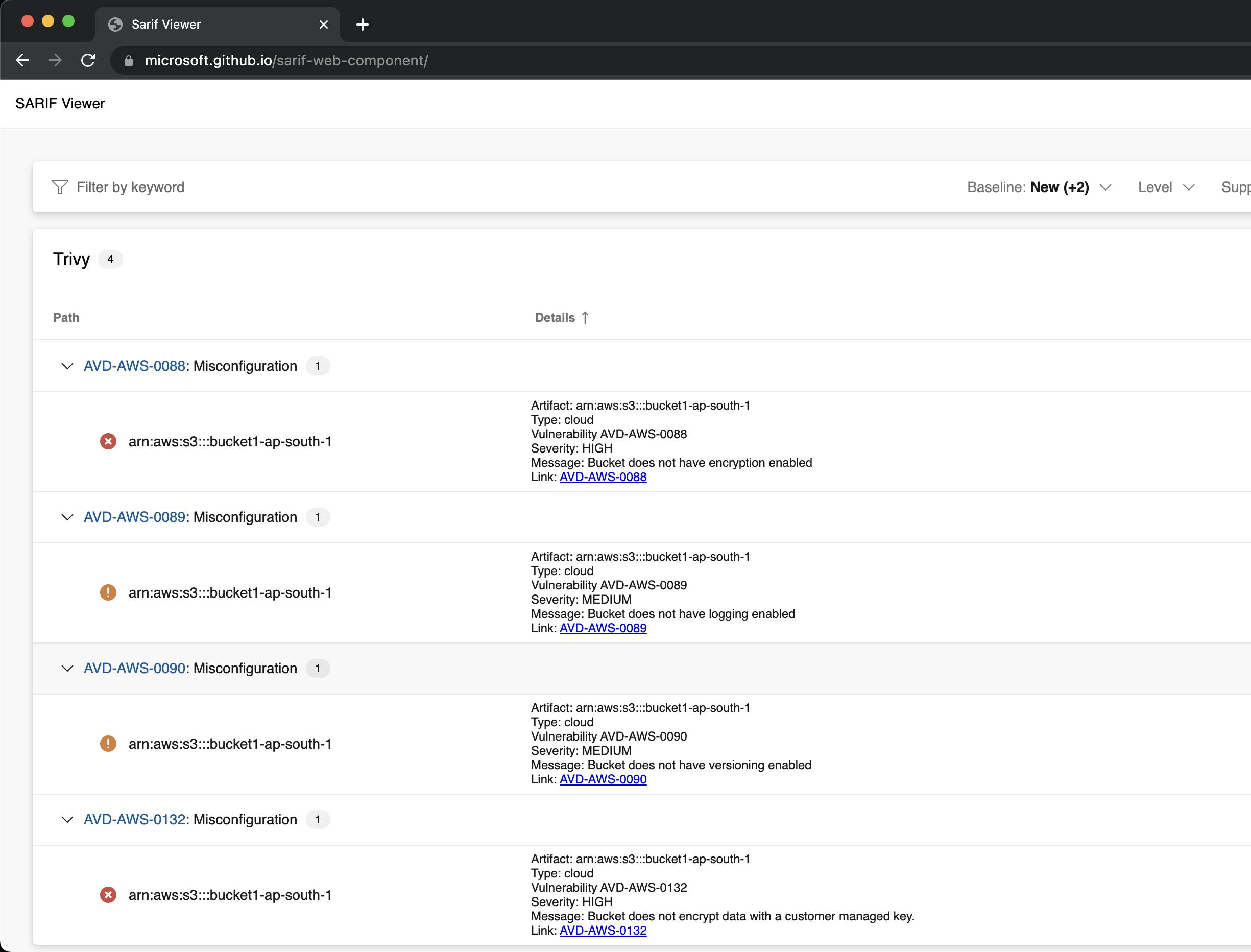
Sarif format allows us to view things visually better.
trivy aws --service=s3 --format=sarif --output=aws-s3-output.sarif
NOTE: If you have multiple misconfigurations/sensitive information in your output, DO NOT upload the results to an online website. Try setting up a local sarif viewer.
I don't have any sensitive information in my output, so I'm uploading them to an online sarif viewer from Microsoft. The output is clean & simple to digest.
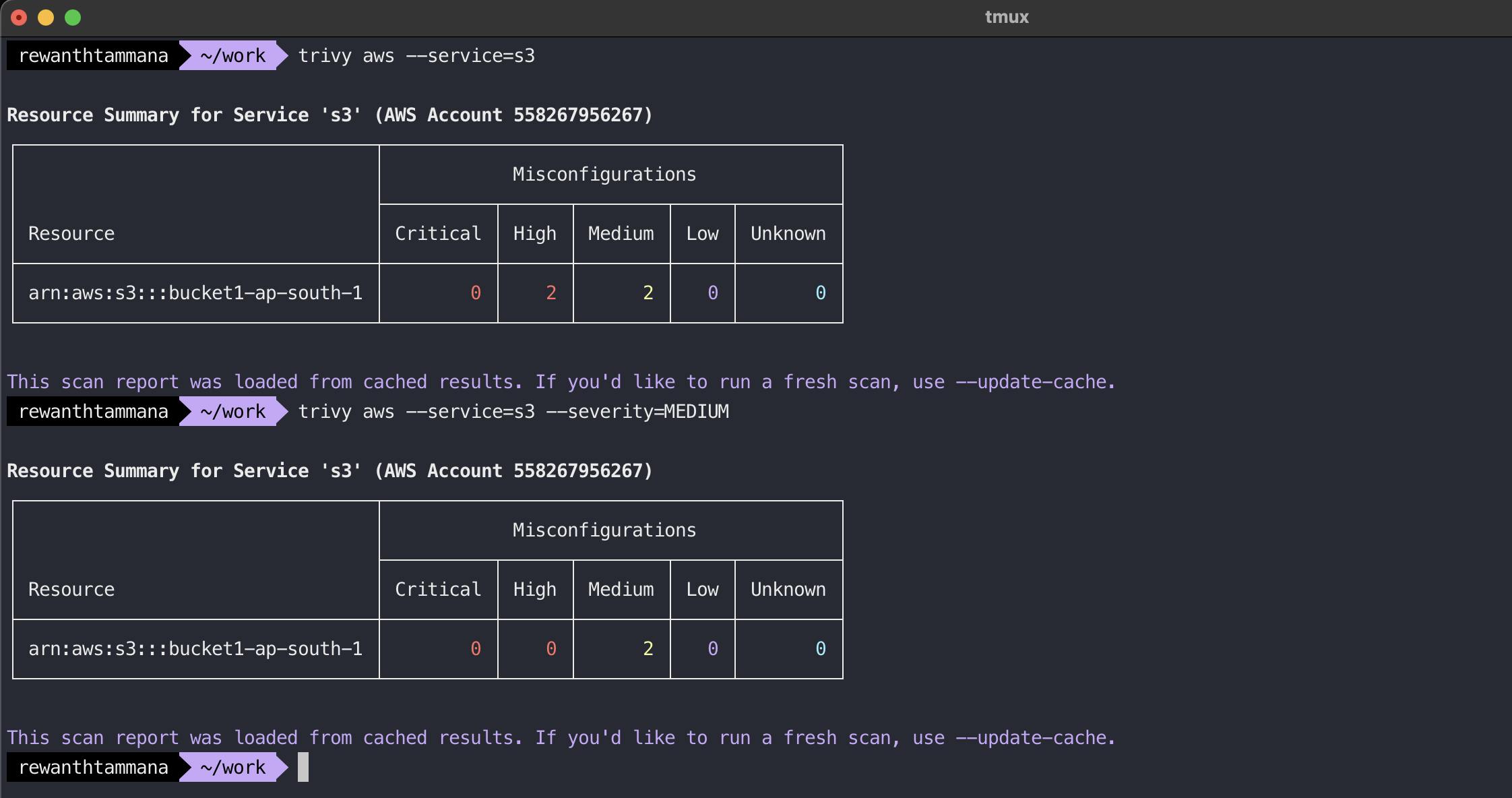
Filter results based on vulnerability severity
trivy aws --service=s3
trivy aws --service=s3 --severity=MEDIUM
More features
Trivy got several features like updating the local cache & filters like account, arn, endpoint, etc.
References
https://aquasecurity.github.io/trivy/v0.31.0/docs/cloud/aws/scanning/ https://docs.aws.amazon.com/securityhub/latest/userguide/securityhub-standards-cis.html
Conclusion
This is a massive enhancement from Trivy to integrate cloud/IaC scanning features into its arsenal. Though it's in the experimental phase, the scanning coverage & features are impressive. We can be sure Trivy plans to integrate more features related to AWS & move to other cloud provider integrations, thus making it the center for scanning universe.